Analysis of the RFID system data reading rate improvement plan
1 Introduction
Radio Frequency (Radio Frequency) refers specifically to electromagnetic waves with a certain wavelength that can be used for radio communications. Radio frequency identification technology (Radio Frequency IdenTIficaTIon) is a non-contact automatic identification technology that began in the 1990s. It uses radio frequency signals and spatial coupling (inductive or electromagnetic coupling) or radar reflection transmission characteristics to achieve identification Automatic identification of objects. However, at present, there are still many bottlenecks in the development of RFID, and the low data read rate is one of the main bottlenecks.
This article will analyze the RFID system by introducing the basic composition and working principle of the RFID system. Combined with the problems encountered in the actual application of the RFID system and the reasons that the reader's reading range contains blind spots, different reading points have excess data, and readers interfere with each other, the reason for the low reading rate of the system is proposed. Optimize the hardware configuration, improve the software design, play the role of middleware and integrate other technologies to improve the data reading rate of the RFID system.
2 Basic composition of RFID system
The RFID system consists of at least two parts: an electronic tag (E-Tag / Transponder, also called smart tag) and a reader (Reader / Interrogator, also called reader).
The electronic tag is the data carrier of the radio frequency identification system. The electronic tag is composed of a tag antenna and a dedicated chip for the tag. According to the different power supply methods, electronic tags are divided into active electronic tags (AcTIve tag), passive electronic tags (Passive tags) and semi-passive electronic tags (Semi-passive tags); depending on the frequency, they are divided into low-frequency electronic tags and high-frequency tags. Frequency electronic label, UHF electronic label and microwave electronic label; according to the different packaging forms are divided into * label, linear label, paper label, glass tube label, round label and special-purpose special-shaped label; according to their working mode There are active tags and passive tags.
Readers are devices used to read or write electronic tag information, and can be designed into multiple types of products according to specific usage environments and needs. The reader wirelessly communicates with the electronic tag through the antenna, and can realize the reading or writing operation of the electronic tag identification code and memory data.
A typical reader includes a high-frequency module (transmitter and receiver), a control unit, and a reader antenna. Of course, when the RFID system is actually applied, it needs the support of other hardware devices such as computers and software. Figure 1 is a typical RFID system composition diagram.
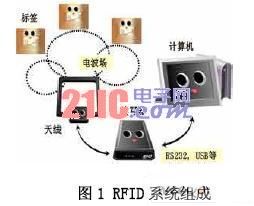
3 Basic model of RFID system
The basic model of the RFID system is shown in Figure 2. The radio frequency carrier between the electronic tag and the reader realizes the spatial (non-contact) coupling of the radio frequency signal through the coupling element. In the coupling channel, according to the timing relationship, energy transmission and data exchange are realized.
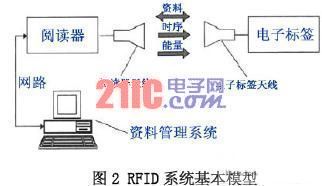
4 Discussion on the reading rate of RFID system
Through the introduction of the RFID system, we believe that the main reason for the low reading rate of the RFID system is that there are blind spots in the reading range of the reader, excess data is stored in different reading points, and the readers interfere with each other. In response to the above problems, we will explore from the following four aspects.
4.1 Reasonably optimize the hardware configuration
In terms of hardware, we must first clarify a problem. That is your true "what is the need". Don't blindly think that "the price is expensive, the larger the reading range, the higher the frequency, the better." As the so-called "tailor-made", the "suitable" one is the best. On the basis of this cognition, you can choose a hardware device that matches your actual needs.
At the same time, consider all RFID tags and readers as a complete "data network", to achieve a reasonable optimization of hardware configuration, so as to maximize the effectiveness of the entire system. Taking the access control system as an example, in order to prevent the reader from having a blind zone in the reading range, which may cause a missed reading, the number of readers or antennas can be increased to compensate for the defect in the reader's reading range; in order to prevent Readers interfere with each other, and the reader or antenna can be relatively isolated in space to avoid mutual interference. In addition, according to actual needs, by appropriately adjusting the antenna layout and antenna transmission power, the data reading rate of the RFID system can also be improved.
4.2 Improve software design
At present, the hardware configuration of the optimized RFID system can basically meet the needs of data reading rate, and as the price of readers decreases, end users can easily deploy a large number of readers in their application sites, which not only solves Read the questions and get more useful information from these systems. But the new problem that comes with it is: redundant data reading or cross data reading. A brief description of the problem is, "A label that should not be read at a certain location was read by a reader that should not read this label."
The core of the LV positioning logic is based on "picking out the required read data from the spatial position while filtering out the unnecessary read data". The result is that the correct and precise tag position is extracted from the results obtained by all RFID readers. In short, the LV positioning logic is a software algorithm based on eliminating the "redundant" read data based on the data set that the entire reader system resides. For the problem of conflicts caused by overlapping working ranges between multiple readers, Colorwave algorithm gives a good solution.
For electronic tag conflicts, in the high-frequency band, the anti-collision algorithm of the tag generally uses the classic ALOHA protocol. Labels using the ALOHA protocol can avoid conflicts by choosing a method of transmitting information to the reader after a random time; in the UHF frequency band, tree bifurcation algorithms are mainly used to avoid conflicts. In addition, other optimization settings can be made to the software. For example, in the electronic ticket system, the scanning time interval of the reader can be designed to work by adaptively adjusting the scanning time through software. For the case of high traffic volume, the software can be used to speed up the scanning frequency of the reader to prevent missed readings; in the case of low traffic volume, the scanning frequency can be relatively reduced to avoid redundant data. .
4.3 Play the role of middleware
RFID middleware occupies a nerve center in various RFID industrial applications. RFID middleware is a message-oriented middleware (Message-Oriented Middleware, MOM). Information is transmitted from one program to another program in the form of messages. RFID middleware plays an intermediary role between RFID tags and application programs. From the application side, a set of common application program interfaces (APIs) provided by the middleware can be used to connect to a reader to read tag data.
Therefore, even if database software or back-end applications that store RFID tag information are added or replaced by other software, or even when the types of RFID readers increase, the application does not need to be modified. This not only effectively solves the problem of data read rate, but also saves other problems such as the maintenance complexity of many-to-many connections. RFID middleware will have very good development prospects in the future in service-oriented architecture (SOA: Service Oriented Architecture Based RFID) and business information security issues.
4.4 Integration with other technologies
Integration with sensor technology
In the next few years, an important application trend of RFID is the combination of RFID and sensors (such as sensors that measure temperature and pressure), which has been implemented abroad. Because RFID has poor anti-interference, and the effective distance is generally less than 10m, this is a limitation to its application. Combining WSN (Wireless Sensor Network) with RFID and using the former's effective radius of up to 100m to form a WSID network will greatly compensate for the deficiencies of the RFID system itself.
Integration with WIMAX, 3G, GPS and other communication technologies
The simple definition of WiMAX (Worldwide Interoperability for Microwave Access) is a wireless broadband data transmission system. The wireless service range of WiMAX can be as far as several kilometers under the condition of maintaining high data traffic in urban areas. Its performance far exceeds the existing wireless network technology. The service range of directional communication connections can maintain a certain data flow. Reaching 50 km, WiMAX technology is considered to be the best backup solution for DSL UMTS connection due to its extremely high performance.
The integration of WiMAX, 3G, GPS and RFID is constantly advancing with the active participation of all parties. RFID tags have the characteristics of small size, large capacity, long life and reusability, and can support fast read and write, non-visual identification, mobile identification, multi-target identification, positioning and long-term tracking management. Cost savings and efficiency improvements have made RFID technology an important entry point for various industries to achieve informatization. They will build a wireless broadband network that can meet the needs of multiple application environments and generate rich applications, expanding the application field of RFID technology.
Fusion with biometrics
Biometrics is a solution that uses automatic technology to measure its physical characteristics or personal behavior characteristics for identity verification, and compares these characteristics or characteristics with database template data to complete authentication. The biometric identification system captures the biometric samples, the only features will be extracted and converted into digital symbols, and these symbols are stored as personal feature templates. People interact with the identification system and authenticate their identities to determine whether they match or not. At present, commonly used biometric recognition technologies include fingerprints, palm prints, face, voice, retina, signature recognition and so on.
In short, the integration of RFID systems with other technologies is imperative, and tremendous results have been achieved. Solve the problem of low data reading rate of RFID system, will definitely make RFID technology widely used, and eventually will be as deep as the barcode technology and slowly extend to all aspects of various industries, which is crucial for the industry to improve operating efficiency and economic benefits Sex, thereby promoting a new leap in the global economy and having a profound impact on human society.
5 Conclusion
Overall, the future development of RFID systems will be better and better. Although there are still some technical and application problems such as low reading rate, we believe that through hardware optimization configuration, perfect software design, and play middleware A series of measures such as function and integration of other technologies are not difficult to overcome the current problems of RFID. Under the strong market orientation, RFID technology will surely cause a major change in the world. It will become a new economic growth point in the future and will eventually become the largest information technology support for the development direction of Chinese enterprises. It is foreseeable that in the near future, as a global manufacturing base, China will be the world's largest RFID application market in the future. This will be a rare opportunity for domestic scientific research institutions and enterprises.
EDM (electrical discharge machining), is a manufacturing process used to obtain a specific desired shape in metal by applying electrical discharges(sparks),When it comes to using electrical discharge machining, the water serves as a key component. To get the best performance from an Edm Machine, the water must be kept as clean as possible. During the EDM process, some of the metal goes into the water as small particles. The water is filtered and deionized(demineralized) in order to remove those metal atoms. Deionized water helps to promote a higher metal removal rate and enhances the machine`s capacity to deliver a more precise cut. So the EDM water filter is very important component for EDM water filtration system.
Edm Filter,Edm Machine,Edm Machining,Wire Edm Machine
Donguan Bronco Filter Co., Ltd , https://www.broncofilter-cn.com